scan4all: a new vulnerability scanner
Table of Contents
scan4all is a Go-based tool to scan vulnerabilities of all kind.
Features
- Port scanner (using Nmap).
- Password blasting (RDP, SSH, FTP, etc.)
- Web fingerprint scanner.
- Support multiple output formats.
- Cross-platform.
- And more.
Installation
- Ensure Go and Nmap are installed:
# Debian/Ubuntu
sudo apt install golang nmap # Arch Linux
sudo pacman -S go nmap # Fedora
sudo dnf install golang nmap- Then, install scan4all using Go:
go install github.com/hktalent/scan4all@2.6.8- Go to the [Relases page](https://github.com/hktalent/scan4all/releases) to check what is the latest version.3. The application is installed in $HOME/go/bin. To be able to run scan4all without specifying the executable path, you need to add $HOME/go/bin to your PATH. Open $HOME/.bashrc and add a line (or edit it) to edit PATH environment variable:
export PATH="$PATH:$HOME/go/bin"- Execute
.bashrcto apply the changes.
source $HOME/.bashrcUsage
Run scan4all -h to see the help page. Most simple command is:
scan4all -host <hostname or IP address>
# scan4all -host 192.168.122.5
# scan4all -host example.com- To scan all ports (and run some tests) you need to run
scan4allwith root privileges (sudo scan4all -host <hostname/IP>). - You can scan subnets.
scan4all -host 192.168.122.1/24- Specify ports with
-p <ports>(separated by commas).
scan4all -host 192.168.122.5 -p 1000,7000- Output the results to JSON or CSV.
scan4all -host 192.168.122.5 -json -o res.json scan4all -host 192.168.122.5 -csv -o res.csv- Only do port scanning and fingerprint recognition.
scan4all -host 192.168.122.5 -np- Set threads and thread rate
scan4all -host 192.168.122.5 -c 25 -rate 1000- Check https://github.com/hktalent/scan4all/blob/main/static/running.md for more info (it’s in chinese). English automatic translation. You can also run
scan4all -h. - If you run scan4all with root privileges and then run it again but as an ordinary user, a permissions error may display.
scan4all vs. Metasploitable
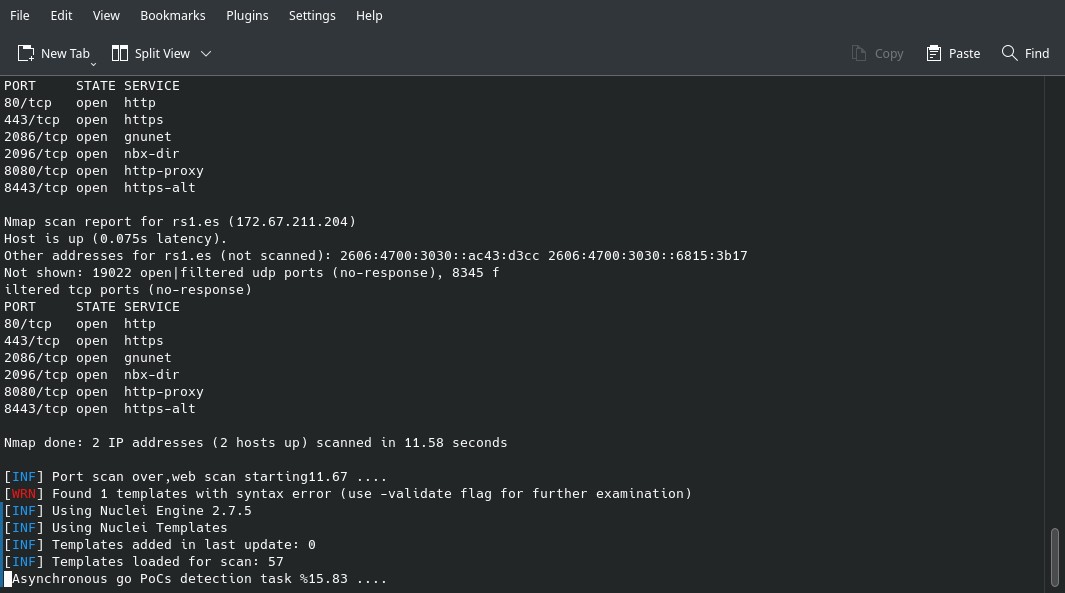
I’m going to test scan4all with the Metasploitable, a vulnerable virtual machine used to test Metasploit Framework tools.
sudo scan4all -host 192.168.1.14After the analysis is over, you can check the red lines (the ones that start with 成功密码破解, meaning “successful password cracking”):
成功密码破解: {"Protocol":"postgresql","Port":5432,"IPAddr":"192.168.1.14","Auth":{"username":"postgres","password":"postgres","Other":{}},"status":true}
...
成功密码破解: {"Protocol":"ftp","Port":21,"IPAddr":"192.168.1.14","Auth":{"username":"ftp","password":"ftp","Other":{}},"status":true}
成功密码破解: {"Protocol":"mysql","Port":3306,"IPAddr":"192.168.1.14","Auth":{"username":"root","password":"","Other":{}},"status":true}And the lines which refer to known vulnerabilities (CVE codes):
[2022-08-06 16:35:38] [CVE-2020-1938] [network] [critical] 192.168.1.14:8009If you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: