Penetration testing with Kali Linux (III): skipfish, sqlmap and John the Ripper
Table of Contents
We continue with our Kali Linux series: in this tutorial we are going to use skipfish, sqlmap and John the Ripper.
skipfish
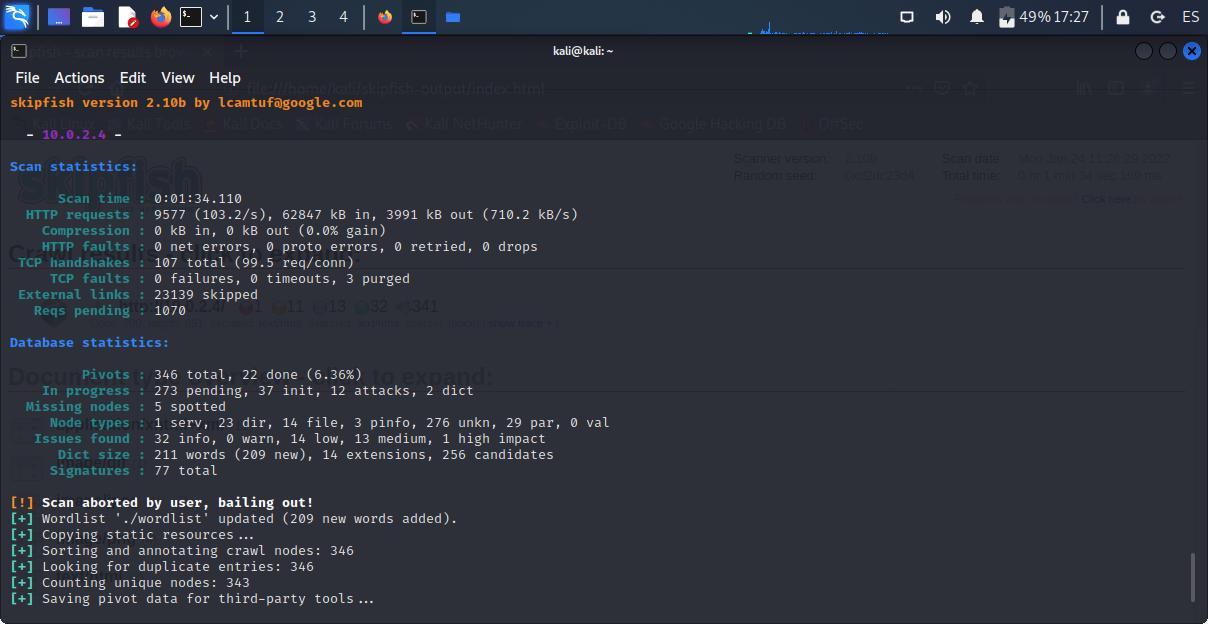
skipfish is a vulnerability scanner you can use to test websites security. It’s very simple to run:
skipfish -W <wordlist> -o <output directory> <url>-W <wordlist>: type the name of an empty file. Skipfish will write any newly learned site-specific keywords.-o <output directory>: a non-existent directory where skipfish will write analysis results.-S <wordlist>: you can add an existent wordlist. File needs to follow this structure.- Type
skipfish -hfor information about more parameters.
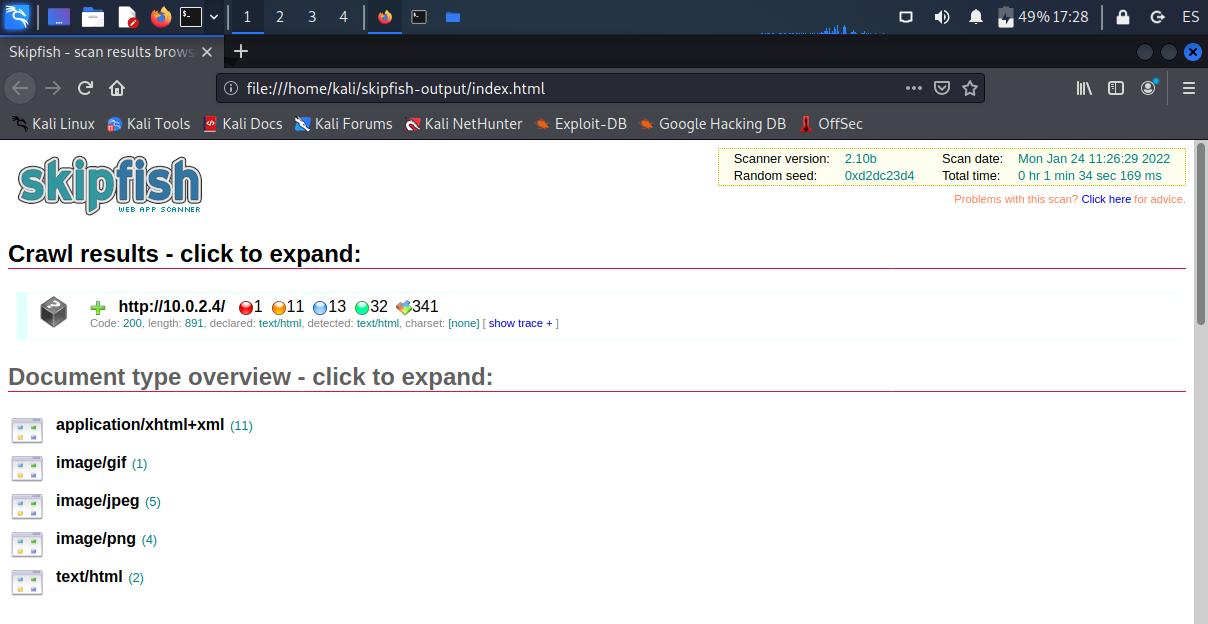
skipfish -W ./wordlist -o ./skipfish-output http://10.0.2.4You can abort the scanning at any time by pressing Ctrl + C. Then, inside the output directory, you can open index.html with a web browser and check the results.
sqlmap
sqlmap detects and exploits a SQL injection. Just type sqlmap -u and a web URL that accepts dynamic user-provided values (e.g.: http://example.com/?id=2).
sqlmap -u http://10.0.2.4/sql/?id=2John the Ripper
John the Ripper (JtR) is a password security auditing and password recovery tool. It’s a bit complicated to use because you need to follow several steps. First, you need to convert the target file (a ZIP, office file, SSH private key, etc.) to a hash by running the appropriate command (some commands are located in /usr/share/john/, others in /usr/sbin/, you can run locate *2john* to list them).
For this tutorial, we are going to create an SSH private key with the password ‘mypassword’.
ssh-keygenNow, we are going to generate a hash file from the key.
python3 /usr/share/john/ssh2john.py testkey > testkey.hashThen, run john with a dictionary file and the hash file (you can copy /usr/share/wordlists/rockyou.txt.gz to your working directory and decompress it). It will use /usr/share/john/password.lst and autogenerated ASCII if no wordlist is specified.
john --wordlist=rockyou.txt testkey.hashUsing default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:02:44 0.01% (ETA: 2022-02-15 05:04) 0g/s 9.416p/s 9.416c/s 9.416C/s daisy1..blueberry
0g 0:00:02:46 0.01% (ETA: 2022-02-15 06:21) 0g/s 9.415p/s 9.415c/s 9.415C/s joyce..danilo
mypassword (testkey)
1g 0:00:03:50 DONE (2022-01-24 13:05) 0.004332g/s 9.357p/s 9.357c/s 9.357C/s oscar1..myfamily
Use the "--show" option to display all of the cracked passwords reliably
Session completed. - As you can see, JtR has found the password (
mypassword).
You can check discovered passwords later with this command:
john -show <hash file>Type john -restore to continue an interrupted session.
More examples of generating a hash file
perl /usr/share/john/pdf2john.pl shared/test1-pass.pdf > test1-pass.hash- ZIP
/usr/sbin/zip2john test.zip > test-zip.hash- KeePass database
/usr/sbin/keepass2john pass-db.kbbx > keepass.hashIf you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: