Single user mode: log in as root using the bootloader
Table of Contents
- Access bootloader
- Edit kernel init options
- Single user mode
- How to avoid unauthorized users to enter single user mode
By tweaking the kernel init options in the bootloader, you can run commands as root on any Linux-based operating system without knowing root password or using ‘sudo’.
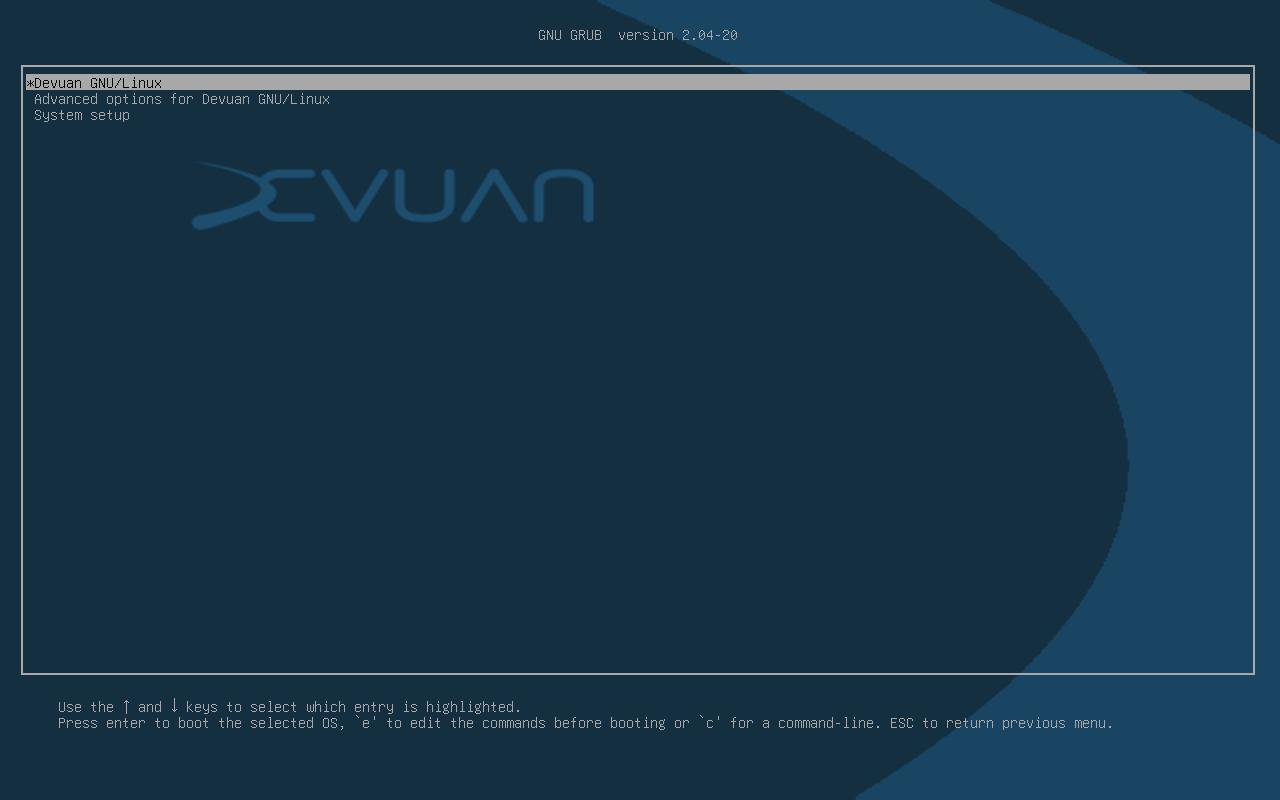
Access bootloader
Boot the computer and avoid the operating system to boot by pressing up or down arrow keys when bootloader (likely GRUB) menu appears. Then, ensure the menu item for booting the operating system is highlighted and press E to edit boot commands.
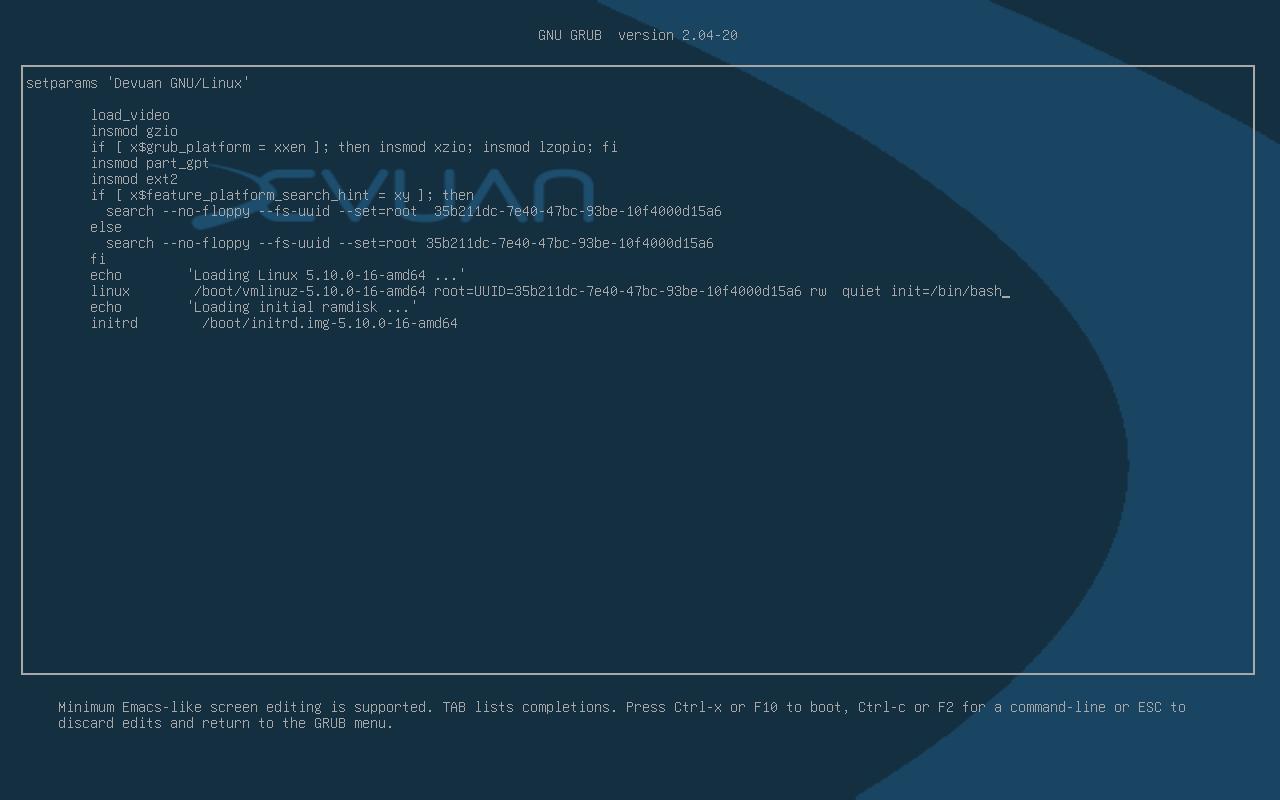
Edit kernel init options
We need to change some kernel init parameters. Using arrow keys, find the line that starts with ‘linux’ and change ro parameter (read-only) with rw (read and write). At the end of the line, add init=/bin/bash (remember parameters are separated by spaces). Finally, to boot, press F10 (check bootloader screen to find which key to press).
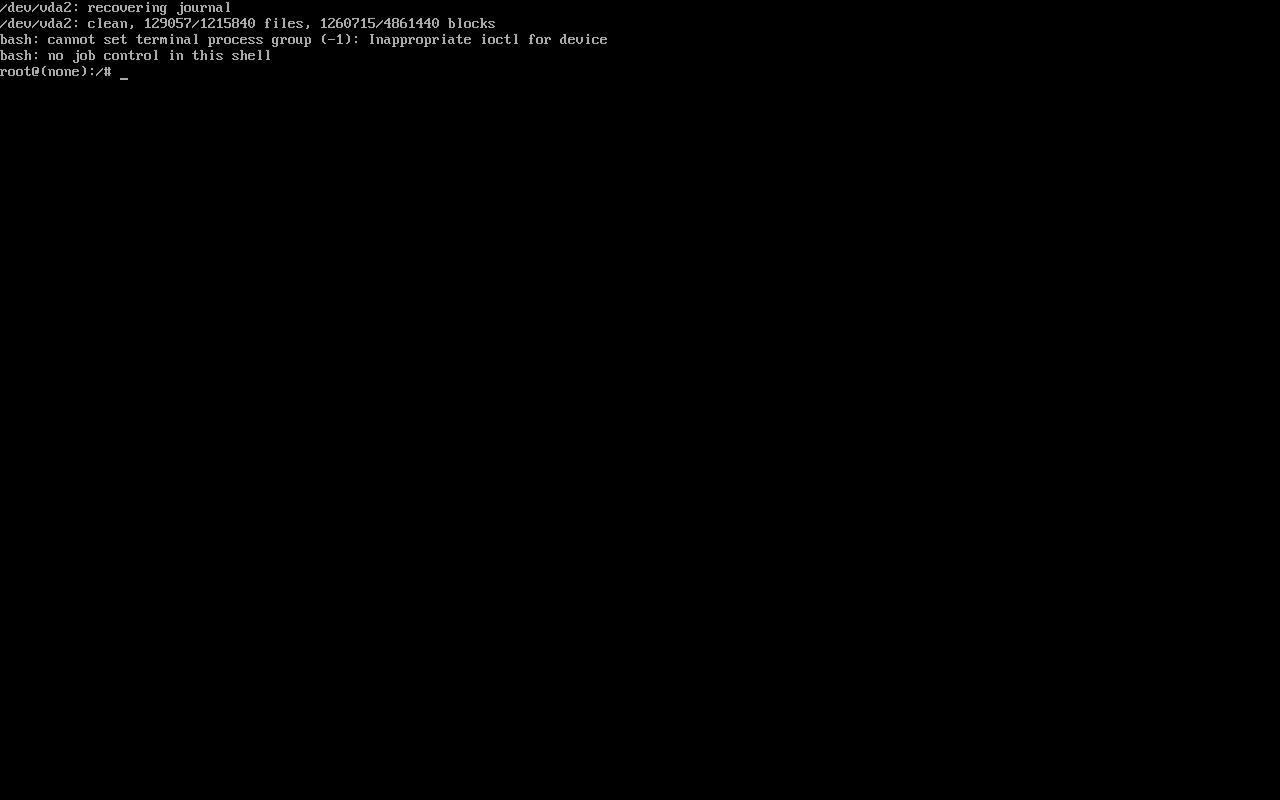
After booting process, you’ll see something like this:
Single user mode
This mode is more restricted than a simple root login and it’s designed to fix critical errors that prevent the operating system to boot correctly. Don’t expect to be able to download and install packages or other network-based tasks but you can do some really important tasks such as changing root password (passwd) or making backups.
How to avoid unauthorized users to enter single user mode
Some bootloaders (like GRUB2) offer basic password protection. The following steps describe how to add password protection to GRUB2 (run the commands as root):
- Create an encrypted password.
grub-mkpasswd-pbkdf2- Copy the password hash (starts with
grub.pbkdf2...). - Edit one of the GRUB config files inside
/etc/grub.d. I recommend you to edit40_custom. Append this:
set superusers="username"- Replace `username` with a user name.4. In the next line, add:
password_pbkdf2 <username> <password>- Replace `<username>` with the previous user name and `<password>` with the copied encrypted password.5. The result will be like this:
set superusers="ricardo"
password_pbkdf2 ricardo grub.pbkdf2.sha512.10000.4BEC- The password has been truncated.6. Apply the changes by running update-grub (Debian/Ubuntu) or grub-mkconfig -o /boot/grub/grub.cfg (Arch Linux, RHEL, etc.) Check your operating system documentation if you don’t know how to proceed.
Now, when an operating system boots or you want to edit a GRUB menu item, you’ll need to add a username and password.
If you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: