Mitigate DoS attacks with Cloudflare and its Firewall rules
Table of Contents
You can reduce the number of Denial-of-Service (DoS) attacks using Cloudflare as a Content Delivery Network (CDN) and a feature called ‘Firewall Rules’.
Register on Cloudflare
If you aren’t already registered in Cloudflare, do it. Basic features are free and you don’t need to pay anything to follow this tutorial. Follow the steps on the page to add a website.
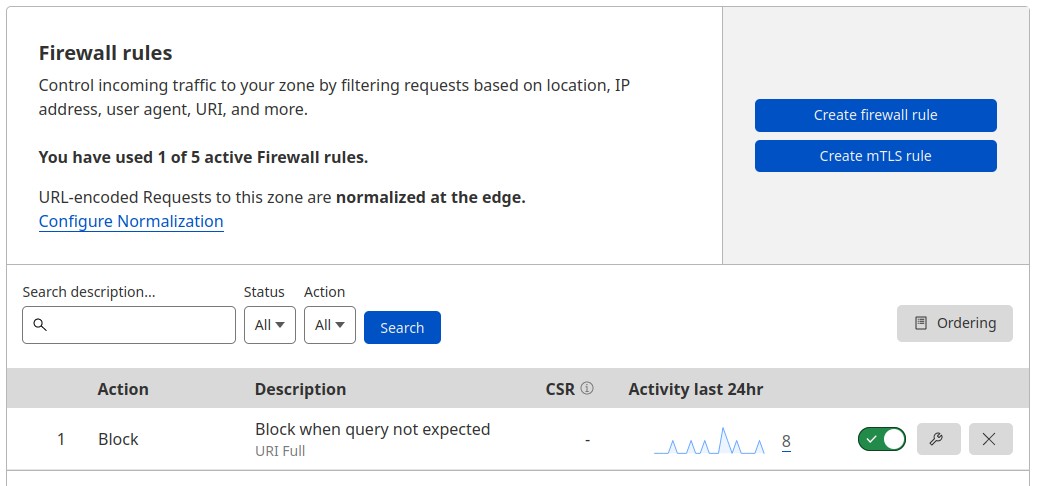
Firewall Rules
Go to Security > WAF (Web Application Firewall). Create a new firewall rule (you can add five for free but you only need one for now). Add a rule name. Now comes the “fun” part. In “When incoming requests match…” is where we add the rules to block or allow access to our website. You can add one or several conditions (based on URI, cookies, country, hostname and much more) and an action (block, managed challenge, allow, etc.) to apply when conditions (all conditions inside a rule) are true.
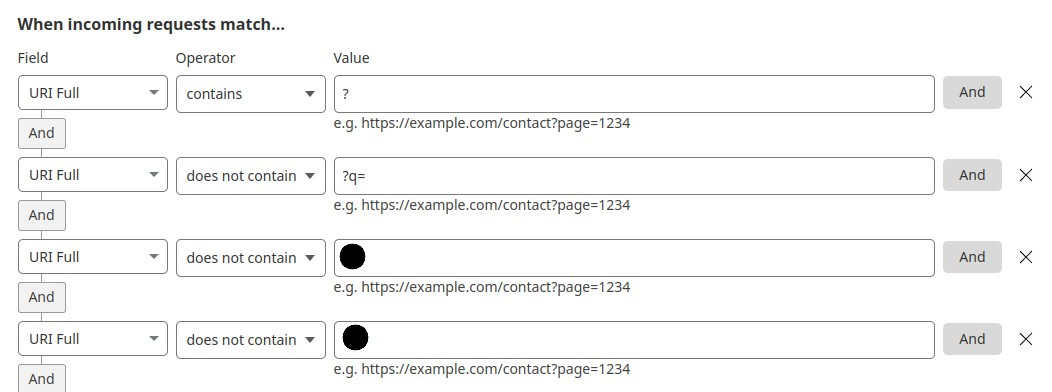
The idea is to block access to any search parameter (?name=value) that we don’t need for our website to work properly. This is because most DoS attacks use search parameters to bypass web browser cache and force the server to send the content, increasing server network traffic.
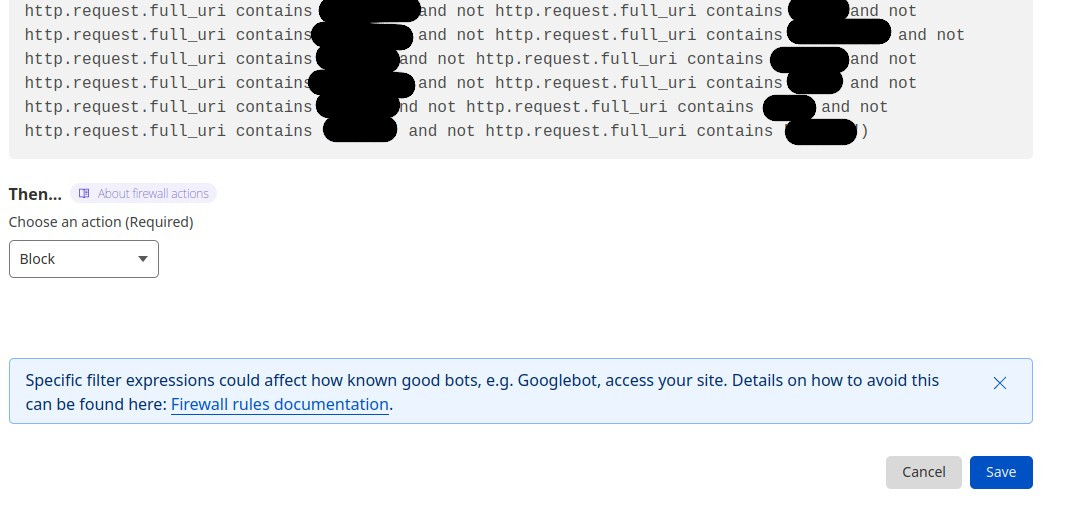
Add a new condition: Inside “Field”, select “URI Full”, in “Operator” select “contains” and, finally, under “Value”, type ”?” (without the quotes). Now we are going to specify the search parameters we need. Click “Add” on the right side of the condition and add a similar condition but, instead of “contains”, select “does not contain”. Type the search parameter (? and the parameter name), and include the “equal” sign (=) if that parameter needs a value.
Do the same with all the needed parameters (remember to click “Add” on each condition because all the conditions need to be true to apply the action). Then, go to the bottom of the page and, inside “Then…” section, select “Block”. Press “Save”.
If you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: