Encrypting a device with LUKS
Table of Contents
- Tools needed
- Setup an encrypted partition
- Open the encrypted partition
- Close the encrypted partition
- Managing encrypted partitions in Desktop systems
In this tutorial we are going to encrypt a USB drive using LUKS, the Linux Unified Key Setup-on-disk-format.
Tools needed
For managing encrypted devices we need cryptsetup (https://gitlab.com/cryptsetup/cryptsetup/). It is probably installed on your system.
Of course we also need a USB drive. We are going to encrypt an already existing and formatted (but empty) partition.
Run the following commands as root.
Note: you can also encrypt virtual disks, check my post.
Setup an encrypted partition
- Plug the USB drive (don’t mount it) and check the name of the partition you want to encrypt, using tools like
lsblk(e.g.:/dev/sdb1). - Run:
cryptsetup luksFormat /dev/sdb1- Type a password.
Open the encrypted partition
- “Open” (unlock) the encrypted partition and map it to a new device (e.g.:
sdb1_encrypted):
cryptsetup open /dev/sdb1 sdb1_encrypted- The new partition is located in
/dev/mapper/.
- Format the unlocked partition (e.g.: FAT32)
mkfs.fat -F32 /dev/mapper/sdb1_encrypted- You can now mount this new partition wherever you want.
mount /dev/mapper/sdb1_encrypted /media/usb- If you try to mount
sdb1instead ofsdb1_encrypted, you’ll see this message:
$ sudo mount /dev/sdb1 /media/usb/
mount: /media/usb: unknown filesystem type 'crypto_LUKS'.
dmesg(1) may have more information after failed mount system call.Close the encrypted partition
- After unmount the partition (
umount /media/usb), run:
cryptsetup close sdb1_encryptedManaging encrypted partitions in Desktop systems
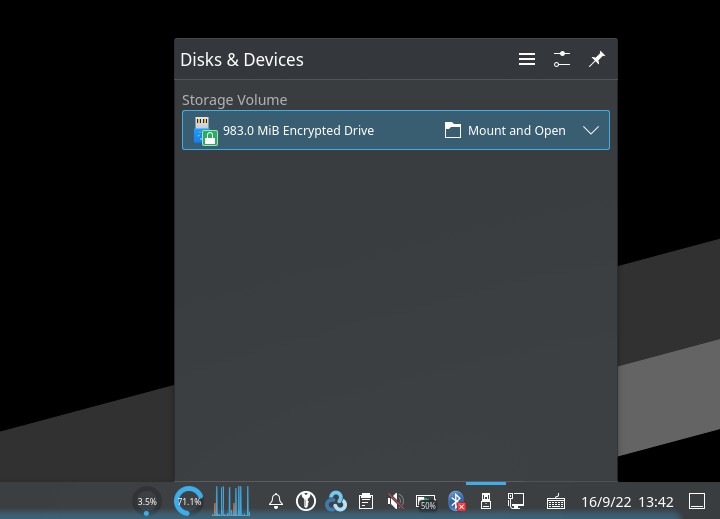
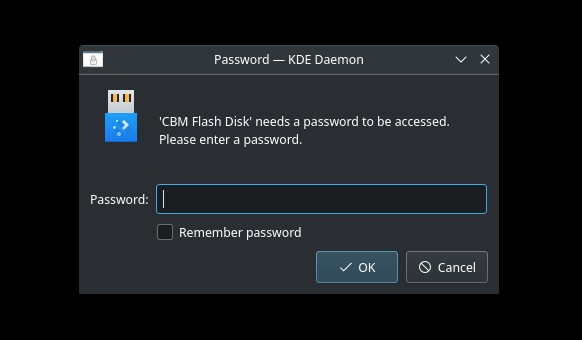
If you use a Desktop Environment like KDE, you can easily mount and unmount an encrypted drive with Dolphin (it will automatically map the partition), so you only need to plug the USB. It will prompt you for the password.
If you have any suggestion, feel free to contact me via social media or email.
Latest tutorials and articles:
Featured content: